Single sign-on with SAML
The availability of this feature depends on your Opendatasoft license or plan.
Opendatasoft allows access to your workspace to be managed through a single sign-on (SSO) authentication solution, and currently supports the SAML and OpenID Connect protocols.
For information on how to map your SSO groups to your Opendatasoft groups, see here.
Register your SAML identity provider on your workspace
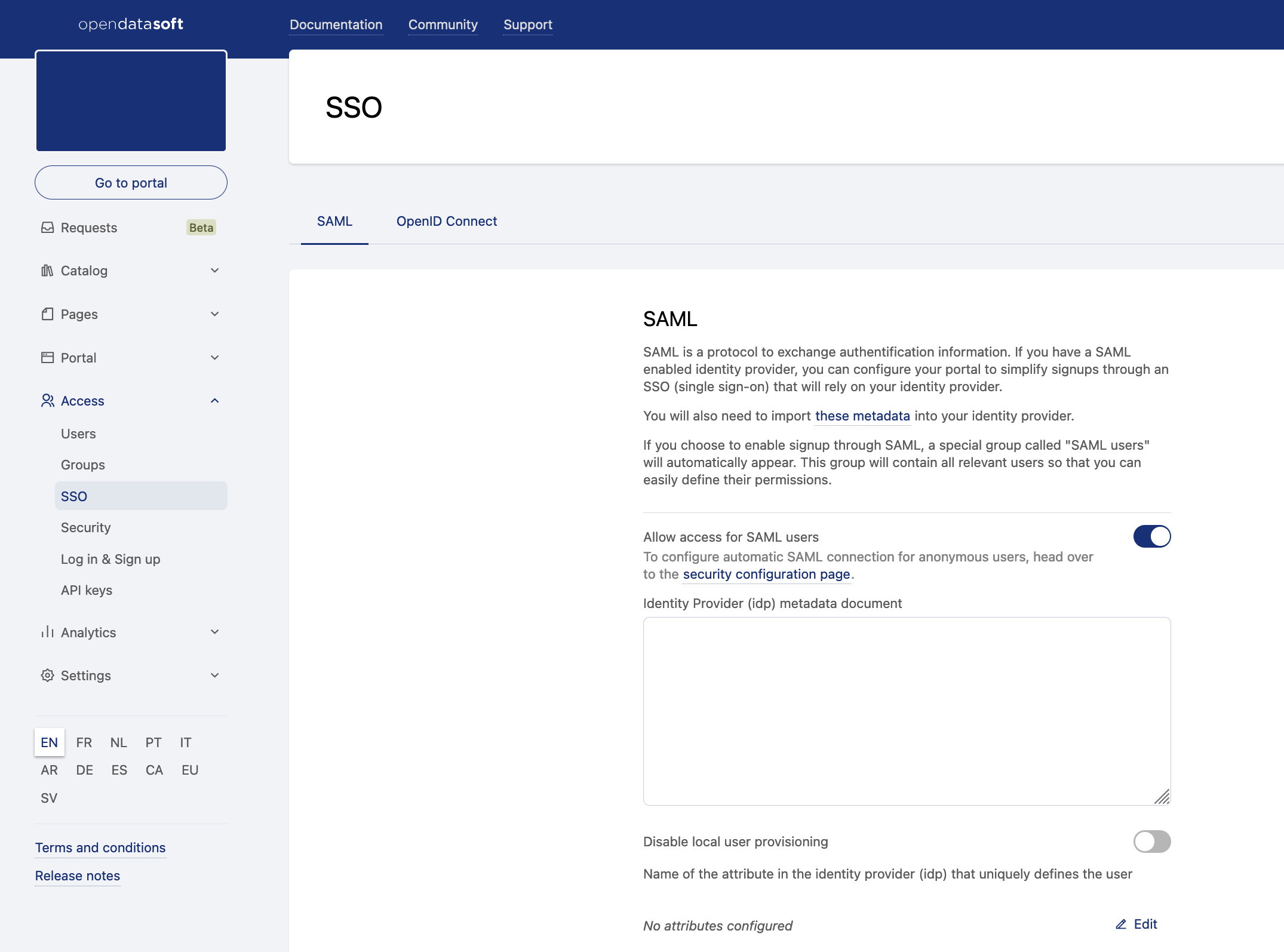
From the back office, go to Access > SSO.
Activate the toggle to "Allow access for SAML users."
Paste your identity provider metadata document into the "Identity provider (idp) metadata document" field.
If you want to disable local user creation, making sure only existing users can connect to the platform through SAML, toggle "Disable local user provisioning."
Enter the set of attributes sent by the identity provider that uniquely define a user in the corresponding field:
For example, if your users are defined by the
FirstNameandLastNameattributes transmitted by your identity provider, enterFirstNamein the field and click +. Then, enterLastNamein the field that appears and click +.If the users are defined by their
NameIDand theNameIDformat used by your identity provider is not transient, leave the field empty.
Enter the attribute mappings for the username, last name, first name, and email address in the corresponding fields. In this step, you need to declare the field names as they are sent by the identity provider:
For example, if your identity provider transmits the connected user's first name in an attribute called
GivenName, enterGivenNamein the "First name" field.If your identity provider doesn't transmit all of these elements, leave the corresponding fields blank. The platform will automatically generate them based on other available attributes.
Enter an access condition:
In the "Attribute to match for the condition" field, enter the name of the attribute to check for.
In the "Value that must be present" field, enter the value for this attribute. If you want to check for the presence of an attribute without value restriction, leave this field blank.
For example, if your identity provider sends a list of
Rolesfor the users and you want only users with a role to be able to connect to the workspace, enterRolesin the "Attribute to match for the condition" field. If you only want users with theDataAccessrole to be able to connect to the workspace, enterDataAccessin the "Value that must be present" field.If you leave both fields blank, no condition is set. Any successful login on the identity provider side will trigger a login on your Opendatasoft workspace.
Enter the URL on which the user can edit their user profile on the identity provider in the "URL for SAML user account configuration" field.
When set, a link to this URL will be shown to the user on their user account page.
If left blank, no URL will be shown to the user on their account page.
Enter a custom EntityID for the Service Provider.
If left blank, the URL of the Service Provider metadata document will be used as the EntityID.
If your identity provider doesn't support EntityIDs in URL format, you can set any EntityID here.
Customize the SAML login link text. If left blank, a localized default message will be displayed.
Registering your workspace on your identity provider
The configuration of the identity provider is implementation-dependant, but it always consists of importing the service provider metadata document to enable an identity federation.
You can download the metadata document for your Opendatasoft workspace on https://<YOUR WORKSPACE>/saml2/metadata.xml.
Single logout
The Opendatasoft platform supports the standard SAML Single Logout flow using the HTTP-Redirect binding:
If supported by the identity provider, a log out from a SAML-connected user will trigger a log out from the identity provider.
Log out requests from the identity provider will trigger a log out of the user on the platform.