Single sign-on with OpenID Connect
The availability of this feature depends on your workspace's license or plan.
Opendatasoft allows access to your workspace to be managed through a single sign-on (SSO) authentication solution, and currently supports the OpenID Connect and SAML protocols.
For information on how to map your SSO groups to your Opendatasoft groups, see here.
Register your OpenID Connect provider on your workspace
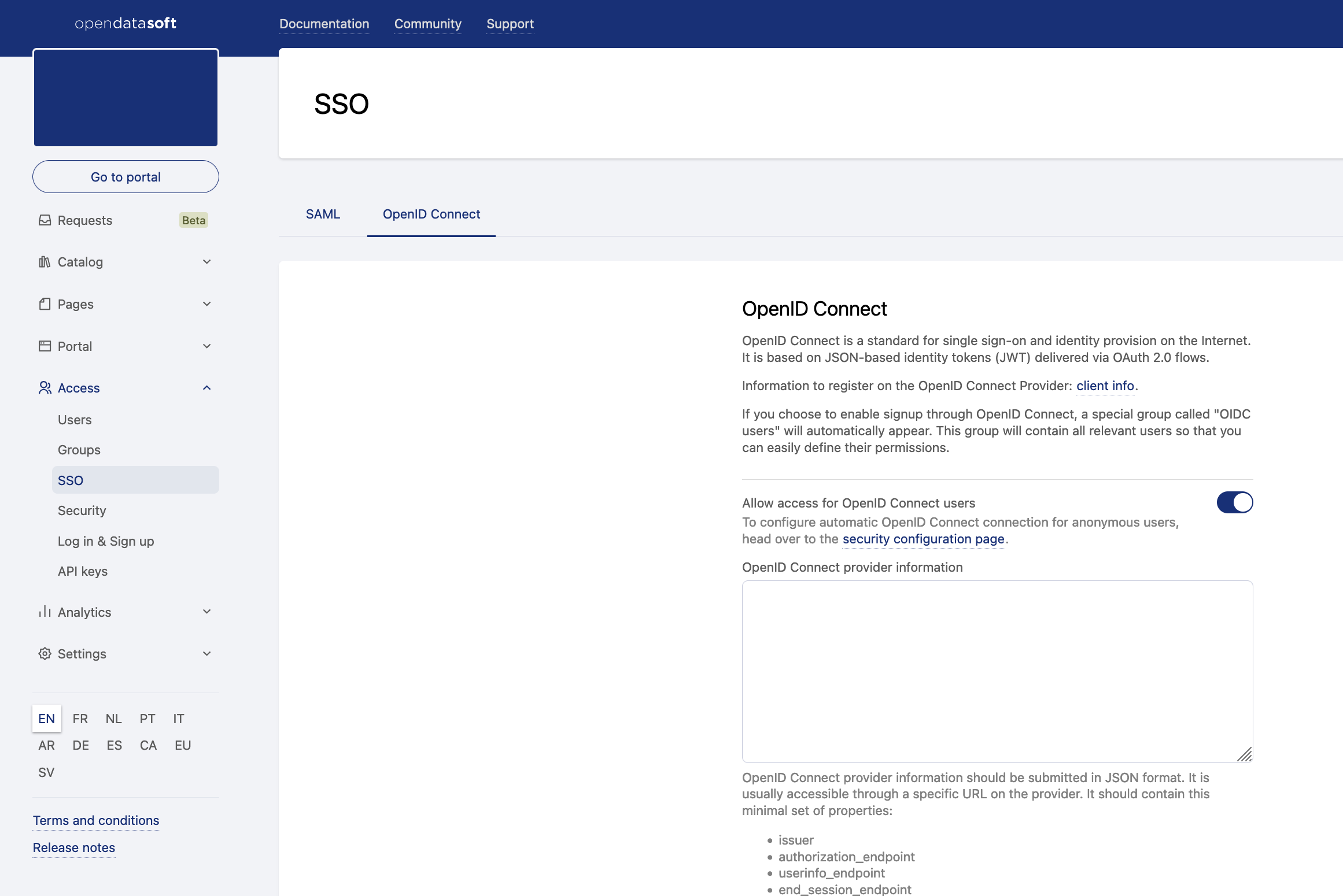
In your back office, go to Access > SSO, then click on the OpenID Connect tab.
Activate the "Allow access for OpenID Connect users" toggle.
Paste your provider discovery document into the "OpenID Connect provider information" field.
This document should be formatted in JSON and can usually be retrieved from your provider endpoint. It must at least contain the following attributes:issuerauthorization_endpointuserinfo_endpointend_session_endpointjwks_uri
If you would like to disable local user creation, making sure only existing users can connect to the platform through OpenID Connect, check the "Disable local user provisioning" checkbox.
Input the application credentials associated with your Opendatasoft workspace.
As you have registered your Opendatasoft workspace as an OpenID Connect client on your provider, you should get a pair of credentials, namelyClient IDandClient secret.
These credentials are used to authenticate requests made by the Opendatasoft platform on the provider endpoint.
Copy these credentials in the "Client ID" and "Client secret" fields.If you would like to use JWT tokens to impersonate API calls on the Opendatasoft platform, check the "Enable direct authentication with JWT bearer tokens" checkbox.
List optional additional scopes
Scopes in OpenID Connect are used to define the set of information (claims) an application would like to receive about a connected user. By default, Opendatasoft uses the following scopes: openid, profile, and email. These scopes make it possible to authenticate a user and to retrieve their email, first name, and last name.
You can use additional scopes to add claims as additional attributes in a user's profile and use them in a dataset's security filters.List optional additional claims
Claims are attributes that are collected during the authentication process and that describe the user. Additional claims are required for group mapping if claims are not already present by default.
By default, Opendatasoft only stores claims received through additional scopes (see point 7 above). You can store additional claims in the user profile. These claims can then be used in a dataset's security filters.
Input the URL on which the user can edit their user profile on the identity provider. When set, a link to this URL will be shown to the user on their user account page. If left blank, no URL will be shown to the user on their account page.
Customize the OpenID Connect login link text. If left blank, a localized default message will be displayed.
Register your workspace on your identity provider
The configuration of the identity provider is implementation-dependant, but it usually consists of specifying on the identity provider the value of the redirection URI, which should be under the form https://<YOUR WORKSPACE>/oidc/authenticate.
Some providers may support a pre-formatted configuration document in JSON format. This document can be downloaded from the following address: https://<YOUR WORKSPACE>/oidc/client_info
Single logout
The Opendatasoft platform supports single logout with OpenID Connect by means of the draft protocol OpenID Connect Back-Channel Logout.