 Getting started
Getting started
 Exploring and using data
Exploring and using data
Exploring catalogs and datasets
Exploring a catalog of datasets
What's in a dataset
Filtering data within a dataset
An introduction to the Explore API
An introduction to the Automation API
Introduction to the WFS API
Downloading a dataset
Search your data with AI (vector search)
Creating maps and charts
Creating advanced charts with the Charts tool
Overview of the Maps interface
Configure your map
Manage your maps
Reorder and group layers in a map
Creating multi-layer maps
Share your map
Navigating maps made with the Maps interface
Rename and save a map
Creating pages with the Code editor
How to limit who can see your visualizations
Archiving a page
Managing a page's security
Creating a page with the Code editor
Content pages: ideas, tips & resources
How to insert internal links on a page or create a table of contents
Sharing and embedding a content page
How to troubleshoot maps that are not loading correctly
Creating content with Studio
Creating content with Studio
Adding a page
Publishing a page
Editing the page layout
Configuring blocks
Previewing a page
Adding text
Adding a chart
Adding an image block to a Studio page
Adding a map block in Studio
Adding a choropleth map block in Studio
Adding a points of interest map block in Studio
Adding a key performance indicator (KPI)
Configuring page information
Using filters to enhance your pages
Refining data
Managing page access
How to edit the url of a Studio page
Embedding a Studio page in a CMS
Visualizations
Managing saved visualizations
Configuring the calendar visualization
The basics of dataset visualizations
Configuring the images visualization
Configuring the custom view
Configuring the table visualization
Configuring the map visualization
Understanding automatic clustering in maps
Configuring the analyze visualization
 Publishing data
Publishing data
Publishing datasets
Creating a dataset
Creating a dataset from a local file
Creating a dataset with multiple files
Creating a dataset from a remote source (URL, API, FTP)
Creating a dataset using dedicated connectors
Creating a dataset with media files
Federating an Opendatasoft dataset
Publishing a dataset
Publishing data from a CSV file
Publishing data in JSON format
Supported file formats
Promote mobility data thanks to GTFS and other formats
What is updated when publishing a remote file?
Configuring datasets
Automated removal of records
Configuring dataset export
Checking dataset history
Configuring the tooltip
Dataset actions and statuses
Dataset limits
Defining a dataset schema
How Opendatasoft manages dates
How and where Opendatasoft handles timezones
How to find your workspace's IP address
Keeping data up to date
Processing data
Translating a dataset
How to configure an HTTP connection to the France Travail API
Deciding what license is best for your dataset
Types of source files
OpenStreetMap files
Shapefiles
JSON files
XML files
Spreadsheet files
RDF files
CSV files
MapInfo files
GeoJSON files
KML/KMZ files
GeoPackage
Connectors
Saving and sharing connections
Airtable connector
Amazon S3 connector
ArcGIS connector
Azure Blob storage connector
Database connectors
Dataset of datasets (workspace) connector
Eco Counter connector
Feed connector
Google BigQuery connector
Google Drive connector
How to find the Open Agenda API Key and the Open Agenda URL
JCDecaux connector
Netatmo connector
OpenAgenda connector
Realtime connector
Salesforce connector
SharePoint connector
U.S. Census connector
WFS connector
Databricks connector
Connecteur Waze
Harvesters
Harvesting a catalog
ArcGIS harvester
ArcGIS Hub Portals harvester
CKAN harvester
CSW harvester
FTP with meta CSV harvester
Opendatasoft Federation harvester
Quandl harvester
Socrata harvester
data.gouv.fr harvester
data.json harvester
Processors
What is a processor and how to use one
Add a field processor
Compute geo distance processor
Concatenate text processor
Convert degrees processor
Copy a field processor
Correct geo shape processor
Create geo point processor
Decode HTML entities processor
Decode a Google polyline processor
Deduplicate multivalued fields processor
Delete record processor
Expand JSON array processor
Expand multivalued field processor
Expression processor
Extract HTML processor
Extract URLs processor
Extract bit range processor
Extract from JSON processor
Extract text processor
File processor
GeoHash to GeoJSON processor
GeoJoin processor
Geocode with ArcGIS processor
Geocode with BAN processor (France)
Geocode with PDOK processor
Geocode with the Census Bureau processor (United States)
Geomasking processor
Get coordinates from a three-word address processor
IP address to geo Coordinates processor
JSON array to multivalued processor
Join datasets processor
Meta expression processor
Nominatim geocoder processor
Normalize Projection Reference processor
Normalize URL processor
Normalize Unicode values processor
Normalize date processor
Polygon filtering processor
Replace text processor
Replace via regular expression processor
Retrieve Administrative Divisions processor
Set timezone processor
Simplify Geo Shape processor
Skip records processor
Split text processor
Transform boolean columns to multivalued field processor
Transpose columns to rows processor
WKT and WKB to GeoJson processor
what3words processor
Data Collection Form
About the Data Collection Form feature
Data Collection Forms associated with your Opendatasoft workspace
Create and manage your data collection forms
Sharing and moderating your data collection forms
Dataset metadata
Analyzing how your data is used
Getting involved: Sharing, Reusing and Reacting
Discovering & submitting data reuses
Sharing through social networks
Commenting via Disqus
Submitting feedback
Following dataset updates
Sharing and embedding data visualizations
Monitoring usage
An overview of monitoring your workspaces
Analyzing user activity
Analyzing actions
Detail about specific fields in the ods-api-monitoring dataset
How to count a dataset's downloads over a specific period
Analyzing data usage
Analyzing a single dataset with its monitoring dashboard
Analyzing back office activity
Using the data lineage feature
 Managing your users
Managing your users
Managing limits
Managing users
Managing users
Setting quotas for individual users
Managing access requests
Inviting users to the portal
Managing workspaces
 Managing your portal
Managing your portal
Configuring your portal
Configure catalog and dataset pages
Configuring a shared catalog
Sharing, reusing, communicating
Customizing your workspace's URL
Managing legal information
Connect Google Analytics (GA4)
Regional settings
Pictograms reference
Managing tracking
Look & Feel
Branding your portal
Customizing portal themes
How to customize my portal according to the current language
Managing the dataset themes
Configuring data visualizations
Configuring the navigation
Adding IGN basemaps
Adding assets
Plans and quotas
Managing security
Configuring your portal's overall security policies
A dataset's Security tab
Mapping your directory to groups in Opendatasoft (with SSO)
Single sign-on with OpenID Connect
Single sign-on with SAML
Parameters
- Home
- Managing your portal
- Managing security
- Single sign-on with SAML
Single sign-on with SAML
Opendatasoft allows access to your workspace to be managed through a single sign-on (SSO) authentication solution, and currently supports the SAML and OpenID Connect protocols.
For information on how to map your SSO groups to your Opendatasoft groups, see here.
Register your SAML identity provider on your workspace
- From the back office, go to Configuration > Signup.
- Activate the toggle to "Allow access for SAML users."
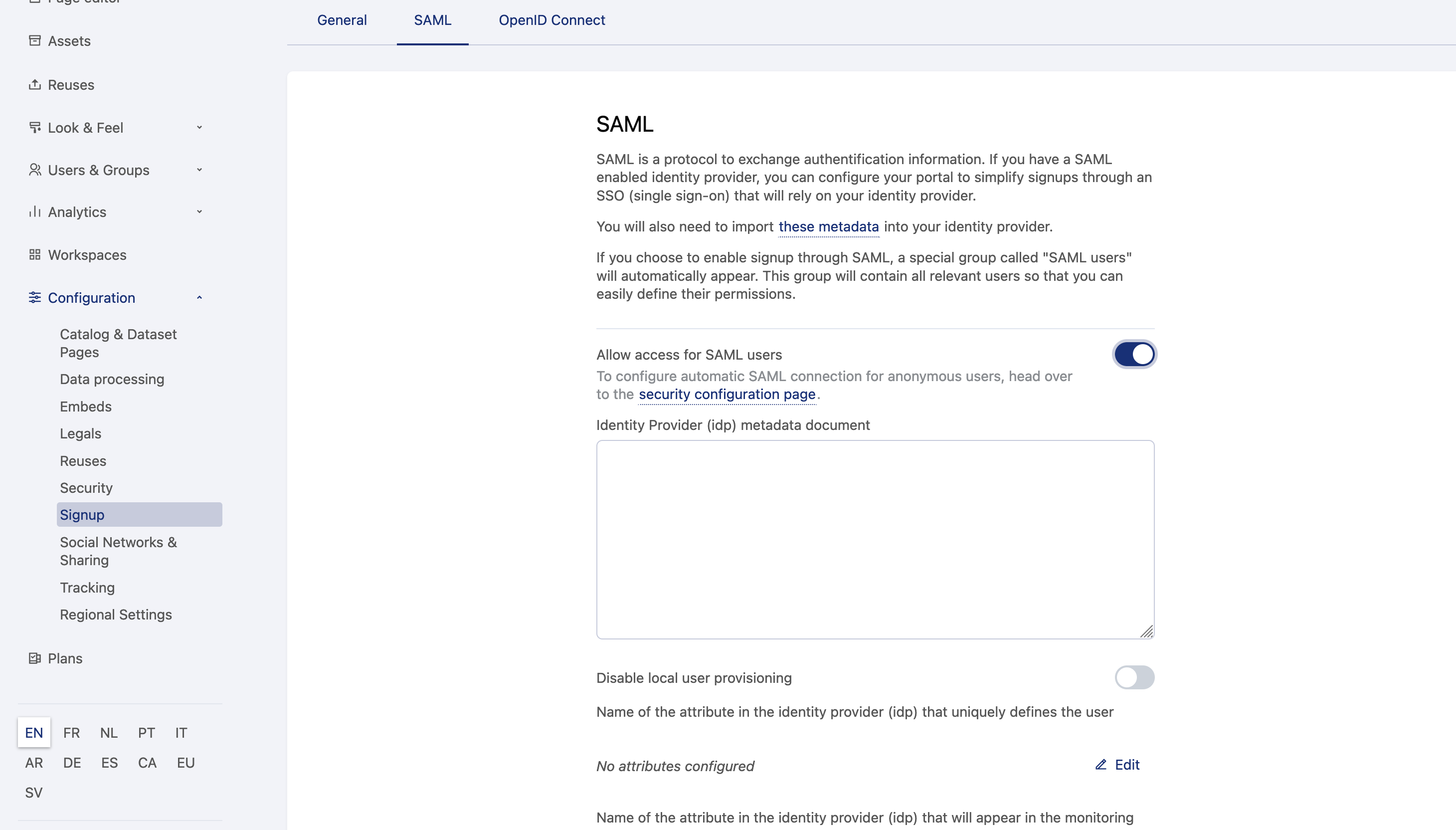
- Paste your identity provider metadata document into the "Identity provider (idp) metadata document" field.
- If you want to disable local user creation, making sure only existing users can connect to the platform through SAML, toggle "Disable local user provisioning."
- Enter the set of attributes sent by the identity provider that uniquely define a user in the corresponding field:
- For example, if your users are defined by the
FirstNameandLastNameattributes transmitted by your identity provider, enterFirstNamein the field and click +. Then, enterLastNamein the field that appears and click +. - If the users are defined by their
NameIDand theNameIDformat used by your identity provider is not transient, leave the field empty.
- For example, if your users are defined by the
- Enter the attribute mappings for the username, last name, first name, and email address in the corresponding fields. In this step, you need to declare the field names as they are sent by the identity provider:
- For example, if your identity provider transmits the connected user's first name in an attribute called
GivenName, enterGivenNamein the "First name" field. - If your identity provider doesn't transmit all of these elements, leave the corresponding fields blank. The platform will automatically generate them based on other available attributes.
- For example, if your identity provider transmits the connected user's first name in an attribute called
- Enter an access condition:
- In the "Attribute to match for the condition" field, enter the name of the attribute to check for.
- In the "Value that must be present" field, enter the value for this attribute. If you want to check for the presence of an attribute without value restriction, leave this field blank.
Rolesfor the users and you want only users with a role to be able to connect to the workspace, enterRolesin the "Attribute to match for the condition" field. If you only want users with theDataAccessrole to be able to connect to the workspace, enterDataAccessin the "Value that must be present" field.If you leave both fields blank, no condition is set. Any successful login on the identity provider side will trigger a login on your Opendatasoft workspace. - Enter the URL on which the user can edit their user profile on the identity provider in the "URL for SAML user account configuration" field.
- When set, a link to this URL will be shown to the user on their user account page.
- If left blank, no URL will be shown to the user on their account page.
- Enter a custom EntityID for the Service Provider.
- If left blank, the URL of the Service Provider metadata document will be used as the EntityID.
- If your identity provider doesn't support EntityIDs in URL format, you can set any EntityID here.
- Customize the SAML login link text. If left blank, a localized default message will be displayed.
Registering your workspace on your identity provider
The configuration of the identity provider is implementation-dependant, but it always consists of importing the service provider metadata document to enable an identity federation.
You can download the metadata document for your Opendatasoft workspace on https://<YOUR WORKSPACE>/saml2/metadata.xml.
Single logout
The Opendatasoft platform supports the standard SAML Single Logout flow using the HTTP-Redirect binding:
- If supported by the identity provider, a log out from a SAML-connected user will trigger a log out from the identity provider.
- Log out requests from the identity provider will trigger a log out of the user on the platform.
